💣 Testing Your Firewall in 60 Seconds
Cyber Defense & Security Practices, Security Tools & TechnologiesA Lightweight WAF Smoke Test Script That Punches Holes in Your False Sense of Security
No agents. No setup. Just raw HTTP payloads and brutal honesty. Find out if your WAF actually works — or if it’s just security theater.
🎯 The Invisible Weak Link in Your Security Stack: Your WAF
You deployed a Web Application Firewall (WAF), flipped the switch, and walked away like it’s bulletproof. But here’s the harsh truth: most WAFs are more of a checkbox than an actual shield.
In the trenches of web security audits, I’ve seen this play out way too often. Over 70% of WAF setups I’ve tested can be bypassed with basic payload obfuscation or alternative encodings. Think of it like parking a tank outside your house… but leaving the back door wide open.
It’s not that WAFs are useless — it’s that they’re often misconfigured, outdated, or simply not tested after deployment. They become security theater: looking the part while silently failing when a real attacker shows up.
💀 Hackers don’t knock. They test, tweak, and tunnel until they’re inside.
If you’re not regularly stress-testing your WAF — simulating real-world attacks, probing for blind spots — then you’re trusting a wall that might already be full of holes.
Remember: security isn’t a set-it-and-forget-it game. It’s a live battlefield. And the WAF? It’s just one weapon — only as sharp as the hands that wield it.
⚡ 60 Seconds to Truth: Is Your WAF Actually Doing Its Job?
Enter waf-smoke-test.sh — your new favorite shell script that cuts through the noise and answers the only question that matters:
“Is my WAF protecting me, or just pretending?”
In under a minute, this no-nonsense tool:
🧨 Fires off 15 real-world attack payloads — SQLi, XSS, Command Injection, and more
🔍 Highlights what slips through vs. what gets blocked
📊 Calculates a “WAF Security Score” so you know where you stand
🔧 Drops tailored recommendations for AWS WAF and Cloudflare configs
📄 Spits out a clean Markdown report you can drop into a ticket or email — no fluff, just facts
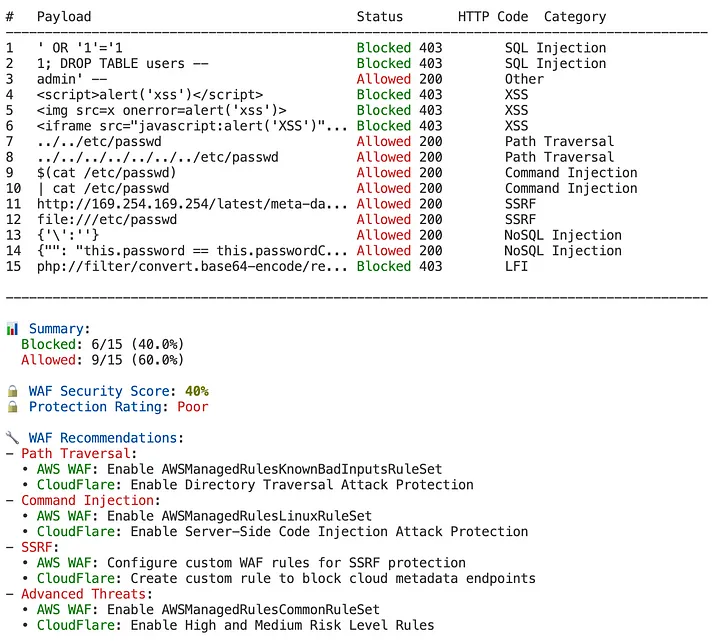
Here’s a sneak peek of the output — plain, punchy, and painfully honest:
🧬 WAF-Agnostic. Hacker-Approved.
The real flex of waf-smoke-test.sh? It doesn’t care what WAF you’re using. This script plays nice with every flavor of firewall:
- 🔥 AWS WAF
- 🌩️ CloudFlare
- ☁️ Azure WAF
- 🧪 Custom-built defenses (Yes, even those “we-coded-it-internally” setups)
Why? Because it doesn’t rely on backend configs, SDKs, or cloud APIs.
It’s pure HTTP voodoo — firing payloads and reading raw server responses like a pentester with x-ray goggles.
👁️ If your WAF can’t block it, this script will expose it. No excuses.
🎯 Real-World Triggers: When to Deploy the Smoke Test
Don’t wait for an incident to realize your WAF is slacking. Here are five critical moments when you must run waf-smoke-test.sh to stay ahead of attackers:
🔄 1. After WAF Rule Updates
Made changes to your WAF rules? Cool. Now prove they work.
./waf-smoke-test.sh "https://your-application.com"
💡 Don’t trust config screens — trust live payload results.
🚀 2. Before Production Deployments
Your app’s going live? Lock it down before it hits real traffic.
./waf-smoke-test.sh "https://staging.your-application.com" -o staging-report.md
📋 Add it to your CI/CD pipeline or pre-launch checklist. One command = peace of mind.
🛡️ 3. During Regular Security Drills
Make WAF testing part of your monthly hygiene. Keep your defenses sharp.
./waf-smoke-test.sh "https://your-application.com" -H "Authorization: Bearer $token"
🔁 Combine it with token-auth and cron to run stealthy, scheduled scans.
☁️ 4. After Cloud Provider Rule Set Changes
Cloud WAFs update under the hood. One tweak can break a rule — or create a hole.
./waf-smoke-test.sh "https://your-application.com" -o post-update-report.md
🧠 Pro tip: Always verify after AWS, Cloudflare, or Azure pushes WAF updates.
🧩 5. When Launching New Features or API Routes
New endpoints = new attack surfaces. Make sure they’re not wide open.
./waf-smoke-test.sh "https://your-application.com/new-feature"
👀 Don’t assume coverage — test each route like a threat actor would.
🤖 Automate the Hunt: WAF Testing in GitHub Actions
Why run it manually when your CI can do it for you?
Add waf-smoke-test.sh to your GitHub Actions workflow and let it auto-check your WAF every push, deploy, or schedule. No more guesswork. Just cold, hard results — on autopilot.
🔗 Ready-to-roll? Fork the full repo here:
🔍 waf-testing GitHub Repo »
Includes the script, example payloads, and a prebuilt CI workflow. Plug and play.
⚙️ GitHub Actions Config: One File to Rule Your WAF
Here’s a drop-in waf-test.yml you can slap into .github/workflows/:
name: WAF Smoke Test
on:
schedule:
- cron: '0 0 * * 1' # Weekly on Mondays
workflow_dispatch: # Manual trigger
jobs:
test-waf:
runs-on: ubuntu-latest
env:
WAF_TEST_URL: https://example.com
steps:
- uses: actions/checkout@v4
with:
# https://github.com/realad/waf-testing
repository: realad/waf-testing
- name: Run WAF test
working-directory: tools/smoke-test
run: |
chmod +x ./waf-smoke-test.sh
./waf-smoke-test.sh "${{ env.WAF_TEST_URL }}" -o report.md
🚀 Getting Started in 3 Steps
🧬 Step 1: Clone the Arsenal
git clone git@github.com:realad/waf-testing.git
cd waf-testing/tools/smoke-test
chmod +x waf-smoke-test.sh
You now hold the 🔑 to weaponize your WAF testing.
💥 Step 2: Launch Your First Recon Run
./waf-smoke-test.sh "https://your-application.com"
Want to simulate real traffic patterns? Add custom headers like a seasoned attacker:
./waf-smoke-test.sh "https://your-application.com" \
-H "User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/18.4 Safari/605.1.15"
🛠️ Step 3: Analyze, Adjust, Dominate
✅ Review the output
🧠 Apply the rule recommendations
🛡️ Lock down your WAF
Repeat. Evolve. Harden.
🧨 Final Word: Stop Trusting. Start Testing.
Security theater won’t stop real attacks. This 60-second smoke test exposes the truth behind your WAF — no deep infosec chops needed.
🔥 Whether you’re on AWS WAF, CloudFlare, Azure, or your own homebrewed fortress — this tool lights up the blind spots and gives you actionable insights to fix them fast.
Don’t wait for a breach to find out your WAF is asleep at the wheel.
Run the test. Own the results. Fortify your stack.