Introduction to Authentication Mechanisms
Career & Learning in CybersecurityImagine this: You log into one app, and suddenly you’ve got access to everything — your email, cloud storage, team dashboard — no need to log in again and again. Feels like magic? It’s not. It’s smart design — and it’s exactly what organizations aim for when they build secure systems.
But there’s more going on behind the scenes.
Every login is a doorway. And if you’re not careful, it’s a doorway that hackers can pick. That’s why companies want one secure system to manage those doors — instead of a messy tangle of passwords and logins everywhere.
Enter the big three: OAuth, OpenID Connect, and SAML.
These aren’t just tech buzzwords. Think of them as the secret agents of authentication — handling who gets in, what they can do, and making sure your password doesn’t get passed around like candy.
- OAuth lets apps access stuff on your behalf — without stealing your password.
- OpenID Connect proves who you are — so the system knows it’s really you.
- SAML links up different systems, like letting your company login work on other platforms.
Together, they help create smooth, secure experiences — and keep the bad guys locked out. Because in the digital world, the right authentication isn’t just helpful… it’s survival.
🕶️ Authentication vs. Authorization
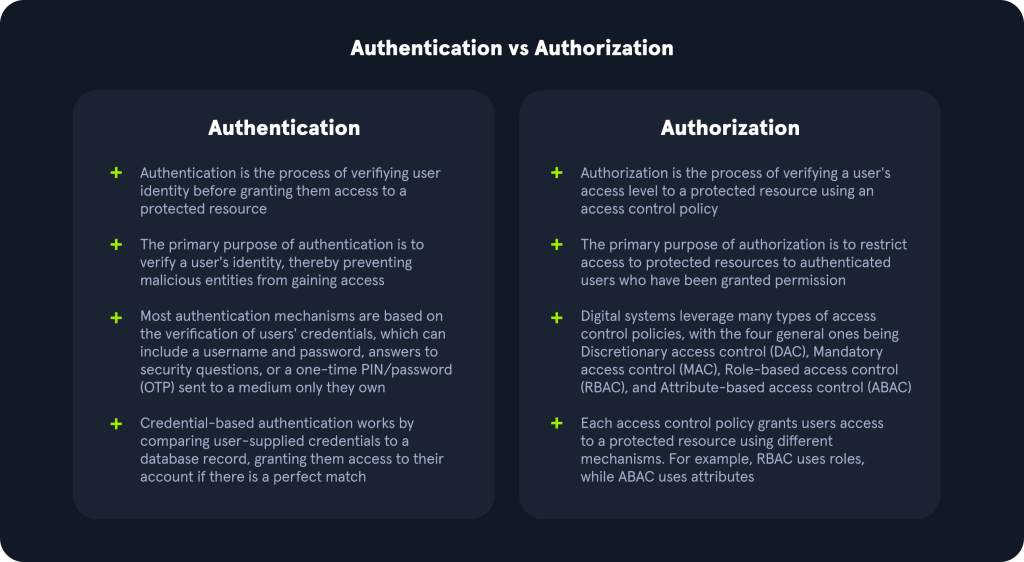
In the digital underground, authentication is your handshake with the system – it’s how you prove you’re not just some script kiddie knocking on the door. Usually, it starts with the oldest trick in the book: username + password. Drop those creds into a login form, and boom – if they match the stored hash, you’re in. It’s like picking the right lock – only this one’s built with salt and SHA algorithms.
But don’t get cocky. Authentication only gets you through the front door. What you do once you’re inside? That’s authorization – and it’s where the real gatekeeping begins.
Authorization defines your access level – basically, whether you can just look around or start flipping switches and rewriting configs. This is controlled by Access Control Models:
- DAC (Discretionary Access Control): The OG method – the owner says who gets what.
- MAC (Mandatory Access Control): Think military-grade – no one’s getting past without clearance.
- RBAC (Role-Based Access Control): The favorite in the app world – you’re assigned a role, and roles come with permissions. You’re a “reader”? Sit back and enjoy the view. “Writer”? Now you’re editing the narrative.
- ABAC (Attribute-Based Access Control): Conditional chaos – access based on attributes like time, location, and device.
So, let’s say the app you just popped uses RBAC. An admin might rock both read and write access, while a basic user is locked in read-only mode. If you’re crafty, you might try to escalate that role – but if the devs did their job, authorization checks will shut down your power grab faster than a firewall on port scan.
Moral of the story? Authentication proves you are who you say you are. Authorization decides what you can do with that identity. And if you’re trying to bypass either – welcome to the red team.
💀 Broken Authentication: When the Lock is Just for Show
In the world of broken authentication, bad implementation is your best friend. It’s shockingly common to stumble across systems that look secure, but crumble the moment you push the right buttons. One misstep in how access control is handled, and suddenly, you’re staring at sensitive data, user accounts, or even root access.
Take an API, for example. If it can’t reliably tell who is making the request, you’ve got a foot in the door – and possibly a clear shot at compromising the entire web app.
Here’s how these locks usually snap open:
- 🚪 Brute-force attacks – Spray and pray with a fat list of usernames and passwords. If there’s no rate limiting, you might just get lucky.
- 🎭 Session token tampering – Mess with unsigned or weakly signed JWTs (JSON Web Tokens). Sometimes all it takes is changing a value and skipping the signature check.
- 🔐 Weak creds & bad crypto – Think “admin/admin” or encryption keys hardcoded in public repos. Yeah, we’ve all seen it.
- 🌐 Token leaks in URLs – Some devs still pass auth tokens in GET requests. One link leak and you’re inside the perimeter.
The basic stuff – like password spraying and login fuzzing – gets you through the door. But this module? We’re going deeper. Advanced authentication attacks, the kind that twist common frameworks and standards until they break, are where real exploit artistry begins.
Think OAuth misconfigurations, SAML abuse, and JWT logic bombs. If broken auth is a gateway, these are the keys to the kingdom.
Welcome to the part where we stop knocking and start kicking doors off their hinges.
🔐 JWT – The Double-Edged Token
JSON Web Tokens (JWTs) are like encrypted sticky notes passed between the client and server — small, fast, and packed with power. Each token has three parts: the header (type and algorithm), the payload (claims like user ID or roles), and the signature (the tamper seal). Together, they form the holy trinity of stateless sessions.
But here’s the kicker: while JWTs look secure, they’re not always used securely.
Developers love them because they’re easy to work with, and they scale well. But attackers love them too, especially when they’re:
- Unsigned or using “alg: none” – yes, some servers still fall for this.
- Using weak keys – guessable secrets, default values, or leaked private keys.
- Not validating expiration – you’d be surprised how many tokens never die.
JWTs are like digital passports — great when verified properly, but deadly if you forge one and no one checks at the gate.
☠️ OAuth – The Trust Game That Can Go Very Wrong
OAuth is the protocol that lets apps say, “Hey Google, can I borrow this user’s data for a sec?” – without the user coughing up their actual password. Cool idea. Dangerous when misused.
This token-based dance lets third-party apps access your account info with limited permissions. But OAuth’s complexity is its Achilles’ heel. Attackers often look for:
- Poor redirect URI validation – leads to phishing, token theft, or account takeover.
- Implicit flow flaws – where access tokens get leaked in URLs.
- Misconfigured scopes – granting way more access than needed.
Used right, OAuth keeps the ecosystem secure. But one misstep in how an app handles those tokens or redirects, and you’ve got yourself an open door to account hijacking on a silver platter.
🧬 SAML – The Corporate SSO Workhorse with an Attack Surface
SAML is like the old-school enterprise wizard of authentication – XML-based, verbose, and still running half the corporate world’s SSO backends.
It lets users log in once (usually through an Identity Provider like Okta or AD FS) and access multiple apps (Service Providers) without re-entering credentials. The IdP sends a digitally signed assertion saying, “Yep, this user is legit.”
Sounds secure? It is — if done right. But attackers know where to poke:
- Signature wrapping attacks – where unsigned assertions are smuggled in.
- Replay attacks – when assertions aren’t time-bound or audience-checked.
- Poor certificate validation – letting malicious IdPs slip forged assertions through.
SAML might be the backbone of many enterprises, but XML signatures and outdated libs are a minefield if not maintained with paranoia.
Final Words: Know the Tokens. Own the Flow.
JWT, OAuth, and SAML are powerful tools – but every token is a potential ticket. If you’re a pentester or red teamer, understanding these standards isn’t optional – it’s essential recon. If you’re on the blue team, lock this stuff down like your job depends on it — because it does.